How does HPV spread?
Original Xu Chao, I’m Chaoski.
After talking about "cauliflower" for so long, the old readers who pay attention to me can be said to be very familiar with it. However, there are still many hin people coming to ask questions about sharp tips every day.
Today, I will tell you enough about condyloma acuminatum once.
Now, if you see friends here, please sit up straight and put down your legs. Let’s begin our little class.

What is condyloma acuminatum?
Condyloma acuminatum, also known as "anal genital warts", usually manifests as soft papules or patches on the external genitalia, perianal skin, perineum or groin.

HPV is a kind of naked double-stranded DNA virus without envelope, belonging to the family Papillomavirus.
At present, among more than 200 subtypes of HPV that have been identified, more than 40 subtypes can spread through sexual contact and infect the anal genital area.
According to the carcinogenicity, HPV is divided into high-risk type and low-risk type. 90%-95% of condyloma acuminatum cases are caused by low-risk HPV types 6 and 11 [1,2].
How is condyloma acuminatum spread?
Human is the only natural reservoir of HPV, and the infected person is the source of HPV infection. There are many HPV in the genital skin mucosa, which is the repository of HPV and the source of virus transmission.
HPV spreads through contact with infected skin or mucosa, and the virus invades epidermal basal cells through tiny scratches. Verruca is not necessary for virus transmission, but it is highly contagious because of its high viral load.
Transmission route
1. Sexual transmission: it is the most important route of transmission, and skin-mucous contact in heterosexual or homosexual sex can cause infection [3].

2. Vertical transmission: It is common for mothers infected with HPV in reproductive tract to transmit it to newborns through placenta and yindao delivery. For example, recurrent papilloma in children’s respiratory tract may be caused by children infected with HPV6/11.
3. Indirect contact transmission: A small number of patients may get sick through non-sexual contact infection. According to some data, 10% of women were infected with HPV before they lived in apricot [4], suggesting that contact between mouth and hands and raw zhi devices can also infect HPV.
HPV infection can enter the incubation period without obvious symptoms and signs. The incubation period is usually 3 weeks to 8 months, with an average of 3 months. Studies have shown that in patients with condyloma acuminatum after new HPV infection, the median time from the detection of HPV6 or HPV11 to the discovery of condyloma acuminatum is 2.9 months [5].
What are the clinical manifestations and symptoms after being infected with condyloma acuminatum?
Appearance and texture: At the initial stage, the lesions of condyloma acuminatum showed local small papules, which gradually increased or increased from the needle to the millet size and spread to the surrounding area. The wart body can be single or multiple, and it can be papillary, cockscomb-shaped, cauliflower-shaped, flat, dome-shaped, filamentous, mushroom-shaped, pedicled, cerebral gyrus-shaped, plaque-like, smooth (especially on penis body) and so on. Condyloma acuminatum is soft to the touch, ranging from 1mm in diameter to several centimeters in size.
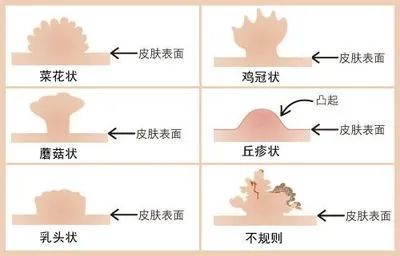
Color: Warts vary in color, ranging from pink to crimson (non-keratinizing lesions), gray (severe keratinizing lesions), brown-black (pigmented lesions) and violet.
Location: For boys, condyloma acuminatum mainly occurs in prepuce, Gui head, coronary sulcus, frenulum, Penis, urethral orifice, perianal region and scrotum. Girls are more likely to occur in Labia, urethral orifice, Vagina mouth, perineum, Vagina wall, cervix and perianal region. If anal sex occurs, warts may appear in the perianal region, anal canal and rectum for the recipient. In addition, if oral sex is performed, warts may also appear in the mouth.
Symptoms: There are generally no symptoms after being infected with condyloma acuminatum, which is one of the reasons why many people do not pay attention to or even delay treatment. A few people may have itching, foreign body sensation, pressure or burning sensation. Due to the increase of brittleness of skin lesions and friction, the skin is broken, soaked, eroded, bleeding or secondary infection, resulting in special odor. In addition, female patients may have increased vagina secretion.
Because condyloma acuminatum is easy to recur, or the warts affect daily life, patients often feel shame, social isolation, anxiety, depression, fear and guilt, and they are also worried that condyloma acuminatum will affect future fertility and increase cancer risk.
In addition, condyloma acuminatum also has a great influence on the feelings between sex partner, which may lead to family conflicts and even lead to the breakdown of relationships.

How to diagnose condyloma acuminatum?
Generally speaking, most patients infected with condyloma acuminatum may have contact history, such as multiple sexual partners, high-risk apricot behavior, or sexual partners with infection history, or close indirect contact history with patients with condyloma acuminatum, and so on. Through these medical histories, combined with the typical clinical manifestations of condyloma acuminatum, the diagnosis can be basically made through face-to-face diagnosis.
For those who cannot be clearly diagnosed by face-to-face examination, they can also be diagnosed by auxiliary examination [6].
1. Acetic acid white test: 3%-5% acetic acid solution is wet-applied or coated on the lesion to be examined and the surrounding skin mucosa. Within 3-5 minutes, if you see a uniform whitening area, it is a positive reaction.
2. Dermatoscope: Dermatoscope can non-invasively, quickly and clearly identify skin lesions, hyperplastic blood vessels and structures that cannot be recognized by naked eyes. Many literatures at home and abroad reported that the diagnostic rate of atypical condyloma acuminatum and tiny condyloma acuminatum by dermatoscope was over 90%.
3. Nucleic acid amplification test: HPV in skin lesions was detected by amplifying HPV-specific genes (L1, E6, E7 region genes), and nucleic acid detection methods included polymerase chain reaction (PCR), real-time fluorescence PCR, and in-situ hybridization test with nucleic acid probes.
4. Pathological examination: For typical skin lesions, histopathological biopsy is unnecessary. If there are some conditions such as uncertain diagnosis, pathological examination can be performed.
In addition, for condyloma acuminatum in anus, vagina and urethra, anoscope, colposcope and urethroscope may be needed for auxiliary examination.
How should condyloma acuminatum be treated?
If you are unfortunately infected with condyloma acuminatum, don’t panic, go to the dermatology department of public hospitals as soon as possible, and sometimes go to urology (boys)/gynecology (girls) for treatment.
The purpose of treating condyloma acuminatum is to remove the wart as soon as possible and eliminate the subclinical infection around the wart as much as possible to reduce or prevent recurrence.

Some people found out that the other person had warts after apricot behavior, and asked if they could use blocking drugs. Unfortunately, there are no blocking drugs for HPV (HIV has related blocking drugs).
Not only are there no blocking drugs, but there are no effective antiviral drugs against HPV at present, so it is impossible to eradicate HPV infection by systematic application of antiviral drugs [7].
If you find yourself growing warts, you can use drugs, physics, surgery, chemistry and other methods to remove them. However, at present, there is no definite evidence to show which treatment scheme is superior to other schemes, and no treatment scheme is suitable for all patients and all warts. All treatment methods have a certain recurrence rate.
According to the suggestion of Clinical Diagnosis and Treatment Guidelines for Condyloma Acuminatum in China (2021 Complete Edition), "The treatment of condyloma Acuminatum can be based on the size, number, location and shape of wart, the patient’s wishes, economic conditions and adverse reactions, and fully consider the individual differences of patients’ age, immune status and compliance, etc." [6].
Drug treatment includes: 0.5% podophyllotoxin tincture, 5% imiquimod cream, 80%-90% trichloroacetic acid solution and so on.
Physical therapy includes: cryotherapy, laser therapy, ionization and high frequency electrotome therapy, etc.
If the number of warts is small, pedicled or large, shearing and excision can be used under local anesthesia, supplemented by electrocautery to destroy the residual warts and control bleeding, without suture.
Photodynamic therapy is suitable for removing small warts and basal therapy after physical therapy to remove large warts. It can be used for the treatment in the cavity such as anal canal, urethral orifice, urethra and cervical canal.

Recurrence and cure
After treatment, condyloma acuminatum is cured by the disappearance of wart body.
However, the recurrence rate of condyloma acuminatum is very high, and the recurrence rate reported by different documents varies greatly, ranging from 10% to 70%. The recurrence rate is the highest within 3 months, and it gradually decreases with time.
At present, most scholars believe that if condyloma acuminatum does not recur after 6-9 months of treatment, the chance of recurrence will be reduced.
Although the recurrence rate of condyloma acuminatum is high, don’t think that you have a "terminal disease" after infection, but have confidence in the treatment.
How to prevent condyloma acuminatum?
Want to prevent condyloma acuminatum, in fact, it is not difficult, four words: "totally".
For people who have no apricot life, there is basically no need to worry about whether they will be infected with condyloma acuminatum. You know, avoiding apricot life is the most reliable way to prevent genital HPV infection.
If you want to have apricot behaviors, don’t engage in unsafe and high-risk apricot behaviors, such as making fire contracts and commercial apricot behaviors. Limiting the number of sex partner can reduce the risk of condyloma acuminatum.
In addition, wearing condoms in apricot life can also prevent condyloma acuminatum to some extent. However, wearing a condom may not be able to protect you, because you may also be infected with HPV in places that are not covered by condoms [8]. Don’t think it’s really safe to wear a condom when unsafe apricot behavior occurs. The safest thing is to avoid high-risk apricot behavior.
Vaccination with HPV vaccine can also prevent HPV infection, and tetravalent or nonavalent HPV vaccine can prevent 90%-95% of condyloma acuminatum. However, if you have been infected with HPV or have grown condyloma acuminatum, it is useless to vaccinate.
I’ve talked so much, I don’t know if you can read it carefully. Mainly because I have received too many inquiries about condyloma acuminatum, I sincerely hope that everyone can protect themselves and others and be healthy.
It’s not easy to write. Don’t you give a "like" or "watching" when you pass by?
references
[1] GARLAND S M, STEBEN M, SINGS H L, et al. Natural history of genital warts: analysis of the placebo arm of 2 randomized phase III trials of a quadrivalent human papillomavirus (types 6, 11, 16, and 18) vaccine [J]. J Infect Dis, 2009, 199(6): 805-14.
[2] BALL S L, WINDER D M, VAUGHAN K, et al. Analyses of human papillomavirus genotypes and viral loads in anogenital warts [J]. J Med Virol, 2011, 83(8): 1345-50.
[3] WRIGHT T C, JR. Natural history of HPV infections [J]. J Fam Pract, 2009, 58(9 Suppl HPV): S3-7.
[4] TAY S K, HO T H, LIM-TAN S K. Is genital human papillomavirus infection always sexually transmitted? [J]. Aust N Z J Obstet Gynaecol, 1990, 30(3): 240-2.
[5] WINER R L, KIVIAT N B, HUGHES J P, et al. Development and duration of human papillomavirus lesions, after initial infection [J]. J Infect Dis, 2005, 191(5): 731-8.
Dermatology and Venereology Branch of Chinese Medical Association, Dermatologist Branch of Chinese Medical Association, Dermatology and Venereology Committee of Chinese Rehabilitation Medical Association. Clinical diagnosis and treatment guidelines for condyloma acuminatum in China (2021 full edition) [J]. chinese journal of dermatovenereology, 2021, 35(4): 359-74.
[7] WORKOWSKI K A, BOLAN G A, CENTERS FOR DISEASE C, et al. Sexually transmitted diseases treatment guidelines, 2015 [J]. MMWR Recomm Rep, 2015, 64(RR-03): 1-137.
[8] GILSON R, NUGENT D, WERNER R N, et al. 2019 IUSTI-Europe guideline for the management of anogenital warts [J]. J Eur Acad Dermatol Venereol, 2020, 34(8): 1644-53.
Disclaimer: Some pictures are from the Internet. If there is any infringement, please contact to delete them.
-End of this period-
Read the original text