Brilliant achievements in agricultural modernization and solid foundation of a well-off society in an all-round way
Realizing the Chinese dream is based on "agriculture, countryside and farmers". General Secretary of the Supreme Leader pointed out that without agricultural modernization, rural prosperity and prosperity, and farmers living and working in peace and contentment, national modernization is incomplete, incomplete and unstable. The "Thirteenth Five-Year Plan" is a decisive period for building a well-off society in an all-round way and achieving the goal of the first century. It is also a crucial period for consolidating the foundation of modern agriculture, adjusting and optimizing the agricultural structure, changing the mode of agricultural development, and striving to improve the quality, efficiency and competitiveness of agriculture.2016year10The National Agricultural Modernization Plan (2016—2020(hereinafter referred to as the "Planning"), focusing on the key areas and weak links of agricultural modernization, put forward five development tasks: innovating to strengthen agriculture, coordinating to benefit farmers, promoting agriculture in a green way, opening up to help agriculture and sharing rich farmers, clearly building a modern agricultural industrial system, production system and management system, and taking the road of agricultural modernization with high output efficiency, product safety, resource conservation and environmental friendliness. In the past five years, under the strong leadership of the CPC Central Committee with the Supreme Leader as the core, agricultural and rural departments at all levels have taken the initiative to adapt to the new normal of economic development, adhered to the general tone of striving for progress while maintaining stability, unswervingly implemented the new development concept, and worked hard to win the battle against poverty and make up for the short-term key tasks of "agriculture, rural areas and farmers" in an all-round well-off society, and concentrated on promoting the implementation and landing of the Plan, taking the structural reform of the agricultural supply side as the main line and constantly improving the agricultural support and protection policy system. We will continue to deepen rural reform, develop and expand the team of new business entities, promote agricultural quality change, efficiency change and power change, and realize the transformation from transforming traditional agriculture to building modern agriculture, from decentralized management by one household to diversified and moderate scale operation, and from extensive development to green ecological sustainable development. According to the assessment, China’s agricultural modernization as a whole is in the initial stage of transformation and leap-forward, and the eastern coastal developed areas, suburbs of big cities, state-owned reclamation areas and national modern agricultural demonstration zones have basically realized agricultural modernization, which indicates that agricultural modernization has stepped onto a new step and laid a solid foundation for the new journey of building a socialist modern country in an all-round way.
First, the comprehensive agricultural production capacity was further consolidated, and the security level of important agricultural products such as grain was steadily improved.
Always take solving the problem of feeding 1.4 billion people as the top priority of governing the country and ensuring the country, and implement it.“Ensure that the grain is basically self-sufficient and the rations are absolutely safe"New food security concept, unremittingly do a good job in food production, focus on the stable production and supply of pigs, coordinate the production and supply of important non-staple foods, and ensure that Chinese’s rice bowl is firmly in its own hands, which provides an important foundation for economic development, social stability and national security.Grain production capacity has reached a new level.Efforts will be made to stabilize policies, area and output, and resolutely shoulder the heavy responsibility of stabilizing national food security. In-depth implementation“Storing grain in the ground and storing grain in technology"Strategy, strictly observe the red line of cultivated land protection, fully implement the special protection system for permanent basic farmland, and ensure that permanent basic farmland remains in15.46More than 100 million mu. Vigorously develop high-standard farmland construction, which has been completed.eightOne hundred million mu of high-standard farmland with high yield and stable yield, which is guaranteed by drought and flood, has been fully completed.10.88One hundred million mu of grain production functional zones and important agricultural products production protection zones have been designated, and a number of grain production core bases have been built. We will earnestly implement the national and provincial seed reserve system for disaster relief and preparedness, and keep the bottom line for dealing with sudden risks such as COVID-19 epidemic, drought and flood disasters. We will further promote the creation of green, high-yield and efficient grain, and integrate and promote improved varieties and fertile fields. Good skills and good methods are matched. We will continue to improve the grain production support policy, adhere to and improve the minimum purchase price policy for rice and wheat, and implement corn and soybeans in four northeastern provinces.“Market-oriented acquisition plus subsidies"Mechanism, continue to increase the scale of incentives for large grain-producing counties, and mobilize the enthusiasm of farmers to grow grain and the government to focus on agriculture and grasp grain. Strengthen the assessment of the governor’s responsibility system for food security, and establish a responsibility mechanism for maintaining national food security in the main grain producing areas, production and marketing balance areas and main sales areas.2020In, China’s total grain output reached66949Ten thousand tons, continuoussixStable in65000More than 10,000 tons; Grain yield reached382.3kilogram/Mu, ratio2015Annual promotion12.1Kilogram; Per capita possession is stable at470More than one kilogram, far higher than internationally recognized.four hundredKilogram safety line.The pig industry has accelerated its transformation.Adhere to the prevention and control of swine fever in Africa, stabilize pig production and ensure supply, continue to strengthen the prevention and control of swine fever in Africa, make overall plans for epidemic monitoring, diagnosis report, emergency disposal, quarantine of origin, transportation supervision, slaughter management and harmless treatment, accelerate the prevention and control in different regions, and accelerate the establishment of modern breeding system, epidemic prevention system, pollution control system and circulation system. The State Council issued the Opinions on Stabilizing Pig Production and Promoting Transformation and Upgrading, implemented the three-year action to speed up the recovery and development of pig production, strengthened the implementation of supporting policies such as land use for pig production, environmental assessment and loan discount, expanded the scope of loan discount for pig farms, and supported large enterprises to develop standardized scale pig breeding.2019Years, years of slaughter500The scale rate of pig breeding above the head has reached53%, slaughter pigs every year2Slaughtering enterprises with a scale of more than 10,000 heads have reached2028Home, accounting for the total slaughter of slaughter enterprises.89.7%。
Good skills and good methods are matched. We will continue to improve the grain production support policy, adhere to and improve the minimum purchase price policy for rice and wheat, and implement corn and soybeans in four northeastern provinces.“Market-oriented acquisition plus subsidies"Mechanism, continue to increase the scale of incentives for large grain-producing counties, and mobilize the enthusiasm of farmers to grow grain and the government to focus on agriculture and grasp grain. Strengthen the assessment of the governor’s responsibility system for food security, and establish a responsibility mechanism for maintaining national food security in the main grain producing areas, production and marketing balance areas and main sales areas.2020In, China’s total grain output reached66949Ten thousand tons, continuoussixStable in65000More than 10,000 tons; Grain yield reached382.3kilogram/Mu, ratio2015Annual promotion12.1Kilogram; Per capita possession is stable at470More than one kilogram, far higher than internationally recognized.four hundredKilogram safety line.The pig industry has accelerated its transformation.Adhere to the prevention and control of swine fever in Africa, stabilize pig production and ensure supply, continue to strengthen the prevention and control of swine fever in Africa, make overall plans for epidemic monitoring, diagnosis report, emergency disposal, quarantine of origin, transportation supervision, slaughter management and harmless treatment, accelerate the prevention and control in different regions, and accelerate the establishment of modern breeding system, epidemic prevention system, pollution control system and circulation system. The State Council issued the Opinions on Stabilizing Pig Production and Promoting Transformation and Upgrading, implemented the three-year action to speed up the recovery and development of pig production, strengthened the implementation of supporting policies such as land use for pig production, environmental assessment and loan discount, expanded the scope of loan discount for pig farms, and supported large enterprises to develop standardized scale pig breeding.2019Years, years of slaughter500The scale rate of pig breeding above the head has reached53%, slaughter pigs every year2Slaughtering enterprises with a scale of more than 10,000 heads have reached2028Home, accounting for the total slaughter of slaughter enterprises.89.7%。 other“shopping basket (for food)"Stable supply of products.Actively develop protected vegetables, promote the upgrading of facilities and equipment, technological integration and innovation, and promote excellent varieties, optimize regional layout, and ensure a balanced supply of vegetables. Implement the quality improvement and efficiency improvement project of horticultural products, build a number of seed breeding bases for fruit, vegetable and tea, promote the transformation of old fruit tea gardens in the dominant fruit, vegetable and tea producing areas, and integrate and promote green, high-quality and efficient technology models.2019In, the output of vegetables, fruits, eggs and aquatic products were respectively72102.6Ten thousand tons,27400.8Ten thousand tons,3309.0Ten thousand tons,6480.4Ten thousand tons, than2015Annual growth8.5%、11.7%、8.6%、4.3%, the output of fruits, vegetables, tea, meat, eggs and fish ranks first in the world, which better meets the ever-increasing diversified consumption needs of the people.Win the COVID-19 epidemic war.Establish an emergency support mechanism in time, make overall plans for production development, production and marketing convergence, circulation and transportation, market regulation, quality and safety, give full play to the role of circulation enterprises and e-commerce platforms, promote the interconnection of wholesale markets, logistics distribution and sales terminals, and ensure that“shopping basket (for food)"The products are available, not out of stock, and not stopped, which ensures the basic stability of the market price and enhances the confidence to meet the challenge of COVID-19 epidemic risk. At the first time, the dispatching mechanism of agricultural products production and market operation in Hubei Province was established, and feed materials such as corn and soybean meal were directly supplied to Hubei during the epidemic period, which provided a solid material guarantee for Hubei Province, especially Wuhan City, to win the anti-epidemic war. The stable production and supply of agriculture during the epidemic in COVID-19 explored an effective way for emergency supply of important agricultural products such as grain.
other“shopping basket (for food)"Stable supply of products.Actively develop protected vegetables, promote the upgrading of facilities and equipment, technological integration and innovation, and promote excellent varieties, optimize regional layout, and ensure a balanced supply of vegetables. Implement the quality improvement and efficiency improvement project of horticultural products, build a number of seed breeding bases for fruit, vegetable and tea, promote the transformation of old fruit tea gardens in the dominant fruit, vegetable and tea producing areas, and integrate and promote green, high-quality and efficient technology models.2019In, the output of vegetables, fruits, eggs and aquatic products were respectively72102.6Ten thousand tons,27400.8Ten thousand tons,3309.0Ten thousand tons,6480.4Ten thousand tons, than2015Annual growth8.5%、11.7%、8.6%、4.3%, the output of fruits, vegetables, tea, meat, eggs and fish ranks first in the world, which better meets the ever-increasing diversified consumption needs of the people.Win the COVID-19 epidemic war.Establish an emergency support mechanism in time, make overall plans for production development, production and marketing convergence, circulation and transportation, market regulation, quality and safety, give full play to the role of circulation enterprises and e-commerce platforms, promote the interconnection of wholesale markets, logistics distribution and sales terminals, and ensure that“shopping basket (for food)"The products are available, not out of stock, and not stopped, which ensures the basic stability of the market price and enhances the confidence to meet the challenge of COVID-19 epidemic risk. At the first time, the dispatching mechanism of agricultural products production and market operation in Hubei Province was established, and feed materials such as corn and soybean meal were directly supplied to Hubei during the epidemic period, which provided a solid material guarantee for Hubei Province, especially Wuhan City, to win the anti-epidemic war. The stable production and supply of agriculture during the epidemic in COVID-19 explored an effective way for emergency supply of important agricultural products such as grain.
Second, the structural reform of the agricultural supply side was further promoted, and the agricultural quality and comprehensive benefits were significantly improved.
Comply with the requirements of upgrading the consumption structure of urban and rural residents, handle the relationship between stabilizing grain production, optimizing agricultural structure and increasing farmers’ income, continuously adjust and optimize the structure of agricultural products and the layout of regional productivity, and strive to promote agriculture from quantity-oriented to quality-orientedThe agricultural structure has been continuously optimized.According to the idea of stabilizing grain and expanding feeding, stabilize corn production in the dominant areas of Northeast China and reduce it cumulatively.“camber"Corn planting area in other non-dominant producing areas5000Ten thousand mu, increase soybean planting area.5000More than ten thousand mu. Guide pig breeding to further concentrate in the main corn producing areas and areas with large environmental capacity, select some typical counties in the main producing areas such as Northeast China, carry out the pilot project of circular development of pig breeding and breeding, demonstrate and guide the orderly transfer of pig production capacity, and reduce the breeding density in the dense water network areas in the south. Start the establishment of the advantage area of characteristic agricultural products, give full play to the advantages of regional resources diversification, and introduce the outline of the construction plan of the advantage area of characteristic agricultural products, which was identified in four batches.308Advantages of agricultural products with China characteristics and667A provincial-level agricultural product advantage zone will accelerate the transformation of resource advantages into product advantages and economic advantages.Herbivorous animal husbandry has developed rapidly.In-depth development of grain to feed subsidies, and vigorously develop the whole plant corn silage and high-quality forage production. Consolidate and improve the development quality of herbivorous animal husbandry in the north, implement grazing prohibition, grazing suspension, rotational grazing and grass-livestock balance system in areas such as the farming-pastoral ecotone in the north, promote improved varieties of animal husbandry in pastoral areas, implement standardized scale breeding projects for beef cattle and mutton sheep, and stabilize the output of high-quality beef and mutton.2020The national output of beef and mutton in was respectively672Ten thousand tons and492Ten thousand tons, than2015Annual growth8.9% and11.8%, the proportion of beef and mutton production in the total output of pigs, cattle, sheep and poultry reached15.2%。 Vigorously implement the dairy industry revitalization plan, support large dairy farming counties to carry out the pilot project of combining planting and breeding in the whole county, and build a number of high-quality milk supply bases, so that the proportion of large-scale dairy farming has reached.64%。 Convene the 4th China Dairy Industry.twentyStrong (D20) Summit to guide the shift from scale expansion to quality and safety. Carry out full coverage monitoring of raw milk quality and safety, the quality of raw milk in large-scale farms has reached the level of developed countries, and domestic dairy brands have gradually won the trust of consumers.The fishery industry has accelerated its transformation and upgrading.Vigorously optimize aquaculture production and spatial layout, change aquaculture methods, actively develop healthy aquaculture, and carry out the construction activities of national-level demonstration farms for healthy aquaculture and demonstration counties for healthy aquaculture.2019year
Consolidate and improve the development quality of herbivorous animal husbandry in the north, implement grazing prohibition, grazing suspension, rotational grazing and grass-livestock balance system in areas such as the farming-pastoral ecotone in the north, promote improved varieties of animal husbandry in pastoral areas, implement standardized scale breeding projects for beef cattle and mutton sheep, and stabilize the output of high-quality beef and mutton.2020The national output of beef and mutton in was respectively672Ten thousand tons and492Ten thousand tons, than2015Annual growth8.9% and11.8%, the proportion of beef and mutton production in the total output of pigs, cattle, sheep and poultry reached15.2%。 Vigorously implement the dairy industry revitalization plan, support large dairy farming counties to carry out the pilot project of combining planting and breeding in the whole county, and build a number of high-quality milk supply bases, so that the proportion of large-scale dairy farming has reached.64%。 Convene the 4th China Dairy Industry.twentyStrong (D20) Summit to guide the shift from scale expansion to quality and safety. Carry out full coverage monitoring of raw milk quality and safety, the quality of raw milk in large-scale farms has reached the level of developed countries, and domestic dairy brands have gradually won the trust of consumers.The fishery industry has accelerated its transformation and upgrading.Vigorously optimize aquaculture production and spatial layout, change aquaculture methods, actively develop healthy aquaculture, and carry out the construction activities of national-level demonstration farms for healthy aquaculture and demonstration counties for healthy aquaculture.2019year By the end of the year, a national demonstration farm for healthy aquaculture will be established.5468A national demonstration county for healthy fishery breeding.forty-nineA, to achieve healthy aquaculture demonstration area proportion increased to65% of the target. Reasonably adjust the fishing industry, optimize the fishing spatial layout, and reduce the fishing intensity.2019National aquaculture output in.5079.1Ten thousand tons, compared with2015Annual growth11%; Fishing yield1401.3Ten thousand tons, compared with2015Annual decline14.3%, the proportion of raising and catching is from2015Annual74∶26Ascend to2019Annualseventy-eight∶22. The fishery industrial structure and development mode have been comprehensively transformed and upgraded. Agricultural cooperation with foreign countries has been deepening. Adhere to two-way opening, win-win cooperation and common development, strive to improve the level and level of agricultural cooperation with foreign countries, and continuously enhance the ability to make good use of both domestic and international markets and resources. Optimize the layout of agricultural foreign cooperation, agricultural field“the Belt and Road"Actively promote the construction, with80More than 20 co-construction countries signed agricultural and fishery cooperation agreements, and agricultural investment cooperation projects were nearlyseven hundredA. Establish an inter-ministerial joint meeting system for agricultural going out, and identifytwentyTwo overseas agricultural cooperation demonstration zones and agricultural opening-up cooperation experimental zones will guide and support powerful enterprises to build platforms and drive domestic enterprises to go out to sea in groups and develop in clusters. Actively respond to Sino-US economic and trade frictions, strengthen trade policy coordination, promote consultations and negotiations, timely study and plan countermeasures such as soybeans and aquatic products, and actively expand import channels.2020The total trade volume of agricultural products in China reached2468.3Billion US dollars, a year-on-year increase.eight%, the pattern of diversified and open agricultural cooperation with foreign countries has been accelerated.
By the end of the year, a national demonstration farm for healthy aquaculture will be established.5468A national demonstration county for healthy fishery breeding.forty-nineA, to achieve healthy aquaculture demonstration area proportion increased to65% of the target. Reasonably adjust the fishing industry, optimize the fishing spatial layout, and reduce the fishing intensity.2019National aquaculture output in.5079.1Ten thousand tons, compared with2015Annual growth11%; Fishing yield1401.3Ten thousand tons, compared with2015Annual decline14.3%, the proportion of raising and catching is from2015Annual74∶26Ascend to2019Annualseventy-eight∶22. The fishery industrial structure and development mode have been comprehensively transformed and upgraded. Agricultural cooperation with foreign countries has been deepening. Adhere to two-way opening, win-win cooperation and common development, strive to improve the level and level of agricultural cooperation with foreign countries, and continuously enhance the ability to make good use of both domestic and international markets and resources. Optimize the layout of agricultural foreign cooperation, agricultural field“the Belt and Road"Actively promote the construction, with80More than 20 co-construction countries signed agricultural and fishery cooperation agreements, and agricultural investment cooperation projects were nearlyseven hundredA. Establish an inter-ministerial joint meeting system for agricultural going out, and identifytwentyTwo overseas agricultural cooperation demonstration zones and agricultural opening-up cooperation experimental zones will guide and support powerful enterprises to build platforms and drive domestic enterprises to go out to sea in groups and develop in clusters. Actively respond to Sino-US economic and trade frictions, strengthen trade policy coordination, promote consultations and negotiations, timely study and plan countermeasures such as soybeans and aquatic products, and actively expand import channels.2020The total trade volume of agricultural products in China reached2468.3Billion US dollars, a year-on-year increase.eight%, the pattern of diversified and open agricultural cooperation with foreign countries has been accelerated.
Third, the agricultural innovation system was accelerated, and the overall level of scientific and technological equipment jumped.
Adhere to the road of independent innovation of agricultural science and technology with China characteristics, deepen the reform of agricultural science and technology system and mechanism, make every effort to overcome key agricultural technologies, promote the deep integration of science and technology with agricultural production, strengthen the integrated application of practical technologies, make great progress in agricultural mechanization, informationization and intelligence, and accelerate the transformation of agricultural development from relying on resources to innovation-driven development.The supporting capacity of agricultural science and technology has been significantly enhanced.Sustainable construction50The technical system of modern agricultural industry of three main agricultural products, form succeed80A number of agricultural science and technology innovation alliances, Nanjing, Taigu, Chengdu, Guangzhou and Wuhan.fivePositive progress has been made in the construction of a modern agricultural industrial science and technology innovation center.“Agricultural silicon valley"Take shape. It has overcome a number of key core technical problems such as wheat scab prevention and control, milk quality and quality safety, and has taken the lead in revealing the mechanisms of plant immunity, African swine fever virus structure and assembly in the world.N7N9Avian influenza vaccine and the first triple live vaccine of porcine viral diarrhea in China have been successfully developed and applied. Basically form a diversified agricultural technology extension system with agricultural technology extension institutions as the leading factor, supplemented by agricultural science and education units, farmers’ cooperatives and agriculture-related enterprises, and demonstrate and popularize Suijing.18Rice, hundred farmers207A large number of major varieties such as wheat, a number of key technologies such as low-crushing mechanized harvesting of corn seeds, biodegradable plastic film replacement technology, and multiple cropping,“fruit—vegetable—tea"A number of advanced models such as ecological breeding.2020In, the contribution rate of agricultural science and technology progress in China reached60%。Modern seed industry“chip"Constantly innovate and break through.The research and application of rice genomics is leading in the world, and the yield per mu of super rice has broken through.1000Kilogram.
succeed80A number of agricultural science and technology innovation alliances, Nanjing, Taigu, Chengdu, Guangzhou and Wuhan.fivePositive progress has been made in the construction of a modern agricultural industrial science and technology innovation center.“Agricultural silicon valley"Take shape. It has overcome a number of key core technical problems such as wheat scab prevention and control, milk quality and quality safety, and has taken the lead in revealing the mechanisms of plant immunity, African swine fever virus structure and assembly in the world.N7N9Avian influenza vaccine and the first triple live vaccine of porcine viral diarrhea in China have been successfully developed and applied. Basically form a diversified agricultural technology extension system with agricultural technology extension institutions as the leading factor, supplemented by agricultural science and education units, farmers’ cooperatives and agriculture-related enterprises, and demonstrate and popularize Suijing.18Rice, hundred farmers207A large number of major varieties such as wheat, a number of key technologies such as low-crushing mechanized harvesting of corn seeds, biodegradable plastic film replacement technology, and multiple cropping,“fruit—vegetable—tea"A number of advanced models such as ecological breeding.2020In, the contribution rate of agricultural science and technology progress in China reached60%。Modern seed industry“chip"Constantly innovate and break through.The research and application of rice genomics is leading in the world, and the yield per mu of super rice has broken through.1000Kilogram. The new round of variety upgrading of major crops has achieved remarkable results, and the number of applications for new variety protection has been continuous.threeRanked first in the world in, the improved varieties of major crops basically achieved full coverage, and the area of self-selected varieties accounted for more than.95%, realizing that China mainly uses China as its grain. The main core species of livestock breeds are derived from the fact that the yield exceeds75%, the self-cultivated Jinghong and Jingfen series of laying hens have reached the international advanced level. The collection and protection system of germplasm resources was initially formed, and the long-term preservation of agricultural germplasm resources reached51Ten thousand copies, the national livestock gene bank collected and preserved all kinds of domestic and foreign livestock genetic materials.90Ten thousand copies. The long-term preservation capacity of the national germplasm resources bank under construction will reach150Ten thousand copies, ranking first in the world. Build three national breeding and seed production bases in Hainan, Gansu and Sichuan, and cultivatefifty-twoA large seed production county and100A regional base, to ensure the national70More than% of the crop seed demand, livestock and poultry breeding farms and core breeding farms can meet the national demand.3/4The demand for livestock and poultry breeding. The core competitiveness of seed enterprises, represented by Longping Hi-Tech and Sinochem Group, has been significantly improved, reaching the national level.“Seed industry aircraft carrier"Take shape.Agricultural mechanization has developed in an all-round way.The State Council issued the "Guiding Opinions on Accelerating the Transformation and Upgrading of Agricultural Mechanization and Agricultural Machinery and Equipment Industry", and implemented the whole mechanization promotion of major crop production.614A demonstration county of mechanization in the whole process of main crop production will promote the mechanized transformation of farmland in hilly and mountainous areas.2019Breakthrough of comprehensive mechanization rate of crop cultivation and harvest in70%, animal husbandry
The new round of variety upgrading of major crops has achieved remarkable results, and the number of applications for new variety protection has been continuous.threeRanked first in the world in, the improved varieties of major crops basically achieved full coverage, and the area of self-selected varieties accounted for more than.95%, realizing that China mainly uses China as its grain. The main core species of livestock breeds are derived from the fact that the yield exceeds75%, the self-cultivated Jinghong and Jingfen series of laying hens have reached the international advanced level. The collection and protection system of germplasm resources was initially formed, and the long-term preservation of agricultural germplasm resources reached51Ten thousand copies, the national livestock gene bank collected and preserved all kinds of domestic and foreign livestock genetic materials.90Ten thousand copies. The long-term preservation capacity of the national germplasm resources bank under construction will reach150Ten thousand copies, ranking first in the world. Build three national breeding and seed production bases in Hainan, Gansu and Sichuan, and cultivatefifty-twoA large seed production county and100A regional base, to ensure the national70More than% of the crop seed demand, livestock and poultry breeding farms and core breeding farms can meet the national demand.3/4The demand for livestock and poultry breeding. The core competitiveness of seed enterprises, represented by Longping Hi-Tech and Sinochem Group, has been significantly improved, reaching the national level.“Seed industry aircraft carrier"Take shape.Agricultural mechanization has developed in an all-round way.The State Council issued the "Guiding Opinions on Accelerating the Transformation and Upgrading of Agricultural Mechanization and Agricultural Machinery and Equipment Industry", and implemented the whole mechanization promotion of major crop production.614A demonstration county of mechanization in the whole process of main crop production will promote the mechanized transformation of farmland in hilly and mountainous areas.2019Breakthrough of comprehensive mechanization rate of crop cultivation and harvest in70%, animal husbandry The mechanization level of aquaculture and aquaculture has reached respectively.34.2% and29.9%;2020The annual comprehensive mechanization rate has reached71%。 Agricultural mechanization is extending from planting and harvesting of main crops to plant protection, straw treatment and drying, and is accelerating from planting to animal husbandry, fishery, facility agriculture and primary processing of agricultural products. Global large-scale application of intelligent agricultural aviation experiment. Information-aided overtaking in agricultural corners. The General Office of the Central Committee of the CPC (hereinafter referred to as the Central Office) and the General Office of the State Council (hereinafter referred to as the State Office) issued the Outline of Digital Rural Development Strategy. The Ministry of Agriculture and Rural Affairs and the Office of the Central Network Security and Informatization Leading Group issued the Digital Agriculture and Rural Development Plan (2019—2025In), a high-resolution remote sensing satellite suitable for agricultural observation was launched to implement the pilot project of digital agriculture construction.“Gaofen No.6"Successfully launched and officially put into use. Remote sensing and other information technologies have been accelerated in the fields of remote diagnosis of animal and plant diseases, supervision of crop rotation and fallow, precision operation of agricultural machinery, and flight prevention of unmanned aerial vehicles, and remarkable progress has been made in intelligent agricultural production, networked management, data management and convenient service. by2020At the end of,12316The service of information entering the village and entering the household has covered all provinces, and public information services are benefiting more farmers.
The mechanization level of aquaculture and aquaculture has reached respectively.34.2% and29.9%;2020The annual comprehensive mechanization rate has reached71%。 Agricultural mechanization is extending from planting and harvesting of main crops to plant protection, straw treatment and drying, and is accelerating from planting to animal husbandry, fishery, facility agriculture and primary processing of agricultural products. Global large-scale application of intelligent agricultural aviation experiment. Information-aided overtaking in agricultural corners. The General Office of the Central Committee of the CPC (hereinafter referred to as the Central Office) and the General Office of the State Council (hereinafter referred to as the State Office) issued the Outline of Digital Rural Development Strategy. The Ministry of Agriculture and Rural Affairs and the Office of the Central Network Security and Informatization Leading Group issued the Digital Agriculture and Rural Development Plan (2019—2025In), a high-resolution remote sensing satellite suitable for agricultural observation was launched to implement the pilot project of digital agriculture construction.“Gaofen No.6"Successfully launched and officially put into use. Remote sensing and other information technologies have been accelerated in the fields of remote diagnosis of animal and plant diseases, supervision of crop rotation and fallow, precision operation of agricultural machinery, and flight prevention of unmanned aerial vehicles, and remarkable progress has been made in intelligent agricultural production, networked management, data management and convenient service. by2020At the end of,12316The service of information entering the village and entering the household has covered all provinces, and public information services are benefiting more farmers.
Four, the development of new business entities, agricultural various forms of moderate scale management level continues to improve.
Adhere to the family management of farmers as the foundation, cooperation and union as the link, and socialized service as the support, give new connotation to the two-tier management system, accelerate the development of intensive, professional, organized and socialized modern agricultural management system, and develop various forms of moderate scale operation steadily.The leading role of new agricultural management entities continues to play.The Central Office and the State Council issued the Opinions on Accelerating the Construction of a Policy System to Cultivate New Agricultural Business Subjects, which are divided into two categories: family farms and farmers’ cooperatives. Focusing on the development of agricultural business entities, we will implement the family farm cultivation plan, carry out in-depth actions to upgrade farmers’ cooperatives, and guide the integrated development of agricultural enterprises, family farms and farmers’ cooperatives around land, capital, labor, technology and products. by2020yearsixIn June, the leading enterprises of industrialization at or above the county level in China were aboutnineTens of thousands of farmers’ cooperatives registered according to law have reached221.8Wanjia, the number of family farm directory system reports exceeds100Tens of thousands, all kinds of new business entities are becoming effective forces to lead moderate scale operation and promote the development of modern agriculture.The socialized service of agricultural production has gradually taken shape.Focus on weak links and serve ordinary farmers, actively develop specialized and socialized service organizations and innovate.
Focusing on the development of agricultural business entities, we will implement the family farm cultivation plan, carry out in-depth actions to upgrade farmers’ cooperatives, and guide the integrated development of agricultural enterprises, family farms and farmers’ cooperatives around land, capital, labor, technology and products. by2020yearsixIn June, the leading enterprises of industrialization at or above the county level in China were aboutnineTens of thousands of farmers’ cooperatives registered according to law have reached221.8Wanjia, the number of family farm directory system reports exceeds100Tens of thousands, all kinds of new business entities are becoming effective forces to lead moderate scale operation and promote the development of modern agriculture.The socialized service of agricultural production has gradually taken shape.Focus on weak links and serve ordinary farmers, actively develop specialized and socialized service organizations and innovate. Service mode and service mechanism, and strive to cultivate and build a three-dimensional multi-functional, complementary, compound and efficient social service system.2019In, the number of socialized service organizations engaged in agricultural production trusteeship in China exceeded.forty-four10,000, and the custody area exceeds15Hundreds of millions of acres, covering small farmers6000Ten thousand households have achieved efficient, convenient and full-scale service; The total area of rural contracted land circulation has reached5.55One hundred million mu, accounting for the country’s rural contracted arable land area.35.9%, realizing centralized contiguous planting and intensive management, effectively promoting the organic connection between small farmers and modern agriculture.Accelerate the cultivation of high-quality farmers.Start the implementation of the project of cultivating high-quality farmers and the action plan of upgrading the academic qualifications of millions of high-quality farmers, and strive to improve and perfect them.“One subject and multiple elements"The education and training system for high-quality farmers has been established, and a cultivation mechanism linking education and training, development support and guidance and encouragement has been initially established. The pertinence, standardization and effectiveness of cultivation have been greatly improved, and the cultivation of high-quality farmers has basically changed from a single technical training to a skill cultivation and management. by2020At the end of, the scale of high-quality farmers in China exceeded.1700Ten thousand, the proportion of high school education or above reached.35%, a large number of high-quality farmers are active in the front line of agricultural production and management, becoming the backbone of new agricultural management entities.The ranks of rural practical talents have further grown.In-depth implementation of the quality improvement plan for rural practical talent leaders, focusing on poverty-stricken areas, and carrying out demonstration training and cumulative training for rural practical talent leaders.eightMore than 10,000 people have trained a large number of leaders who can stay, use and do well in rural areas, which has led all localities to increase the training of practical talents in rural areas. by2019By the end of, the total number of rural practical talents in China was about2300Ten thousand people have provided strong talent support for poverty alleviation and rural revitalization.
Service mode and service mechanism, and strive to cultivate and build a three-dimensional multi-functional, complementary, compound and efficient social service system.2019In, the number of socialized service organizations engaged in agricultural production trusteeship in China exceeded.forty-four10,000, and the custody area exceeds15Hundreds of millions of acres, covering small farmers6000Ten thousand households have achieved efficient, convenient and full-scale service; The total area of rural contracted land circulation has reached5.55One hundred million mu, accounting for the country’s rural contracted arable land area.35.9%, realizing centralized contiguous planting and intensive management, effectively promoting the organic connection between small farmers and modern agriculture.Accelerate the cultivation of high-quality farmers.Start the implementation of the project of cultivating high-quality farmers and the action plan of upgrading the academic qualifications of millions of high-quality farmers, and strive to improve and perfect them.“One subject and multiple elements"The education and training system for high-quality farmers has been established, and a cultivation mechanism linking education and training, development support and guidance and encouragement has been initially established. The pertinence, standardization and effectiveness of cultivation have been greatly improved, and the cultivation of high-quality farmers has basically changed from a single technical training to a skill cultivation and management. by2020At the end of, the scale of high-quality farmers in China exceeded.1700Ten thousand, the proportion of high school education or above reached.35%, a large number of high-quality farmers are active in the front line of agricultural production and management, becoming the backbone of new agricultural management entities.The ranks of rural practical talents have further grown.In-depth implementation of the quality improvement plan for rural practical talent leaders, focusing on poverty-stricken areas, and carrying out demonstration training and cumulative training for rural practical talent leaders.eightMore than 10,000 people have trained a large number of leaders who can stay, use and do well in rural areas, which has led all localities to increase the training of practical talents in rural areas. by2019By the end of, the total number of rural practical talents in China was about2300Ten thousand people have provided strong talent support for poverty alleviation and rural revitalization.
Five, accelerate the development of rural industries to enrich the people, the level of industrial integration and development has improved significantly.
Based on agricultural and rural resources, we should fully tap the various functions and values of rural areas, focus on key industries, gather resource elements, extend the industrial chain, improve the supply chain, upgrade the value chain, and accelerate the construction of a modern industrial system in which agriculture and secondary and tertiary industries cross and merge.Agricultural products processing industry to speed up the layout of advantageous areas.The State Council issued the Opinions on Further Promoting the Development of Agricultural Products Processing Industry to promote the agricultural products processing industry from quantity growth to quality improvement, factor-driven to innovation-driven and decentralized distribution.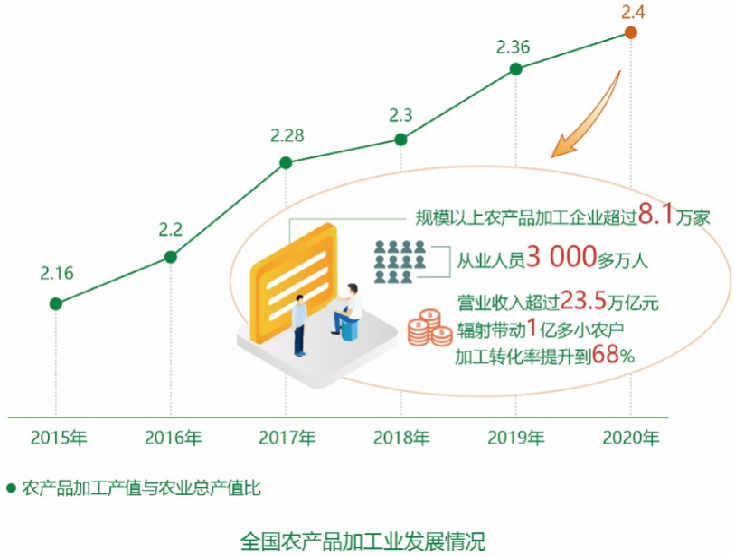 Bureau changes to cluster development. We will implement the promotion of agricultural product processing industry, support farmers’ cooperatives and family farms to develop primary processing of agricultural products, improve the comprehensive utilization level of agricultural product processing by-products, guide large agricultural enterprises to develop deep processing of agricultural products, and basically form a pattern of gradient transfer of agricultural product processing industry to main producing areas, characteristic and advantageous producing areas, key sales areas and key logistics nodes. by2020By the end of, more than.17Ten thousand primary processing facilities for agricultural products, the postpartum loss rate of potatoes, fruits and vegetables from15% reduced tosixBelow%, processing conversion rate from2015Annual65% to2020Annualsixty-eight%。 Operating income of agricultural products processing industry is about23.5One trillion yuan, the ratio of agricultural product processing industry to total agricultural output value reached.2.4∶one.Leisure agriculture and rural tourism have developed rapidly.The multiple functions of agriculture have been continuously expanded, and new industries and formats such as shared agriculture, experience agriculture and creative agriculture have emerged in large numbers, and industries such as science and technology, culture, education, tourism and health care have merged with agriculture across borders. The implementation of leisure agriculture and rural tourism quality projects has created388A national key leisure agriculture county, identified.1216individual“One village and one scene"Beautiful leisure country. Carry out promotion activities in China and beautiful countryside, and promote them cumulatively.nine hundred and seventyA beautiful leisure village with complete functions and outstanding features and1000A boutique tourist route.2019In, the business income of leisure agriculture and rural tourism exceeded.8500100 million yuan, the average annual growth rate.9.8%, directly driven1200Increasing the employment and income of rural labor force has become an important form to expand agricultural functions and enhance rural value.Rural innovation and entrepreneurship have become a craze.The State Council issued the Opinions on Supporting Entrepreneurial Innovation of Returned Rural Workers to Promote the Integrated Development of Rural Primary, Secondary and Tertiary Industries, and supported returning migrant workers, college graduates, retired military personnel, scientific researchers and rural capable people to start businesses in their hometowns.2020In, the number of innovative entrepreneurs who returned to their hometowns reached.1010Ten thousand people, innovative entrepreneurs in the countryside.3000More than ten thousand people. Implementation of rural innovation and entrepreneurship leaders training action, held continuously.fiveAt the National New Farmers’ New Business Innovation Conference, farming experience and e-commerce live broadcast have flourished, and live broadcast agriculture has become a new bright spot in rural economy, providing new kinetic energy for the transformation of agricultural supply chain and the promotion of value chain. by2019At the end of, the number of rural e-commerce registered at or below the county level exceeded.eight hundredTen thousand, the national rural network retail sales reached1.7One trillion yuan, the total retail sales of agricultural products e-commerce reached3975100 million yuan.Rural industrial integration has gradually become a trend.Accelerate the construction of a large-scale economic circle with advantageous industrial clusters, a medium-sized economic circle with modern agricultural industrial parks, and a small economic circle with strong agricultural industries.“Yi Cun yi pin"Micro-economic circle to promote the construction of rural industries“circle"Development pattern, the formation of national, provincial, city (state), county four linkage rural industrial system, realize“Point, line and surface"Combination, organic connection of functions, and regional radiation drive. Accumulate and create characteristic advantageous industrial clusters.50National modern agricultural industrial park151Demonstration Park of Rural Industrial Integration228A town with strong agricultural industry811One, let more employment opportunities stay in the countryside and more value-added benefits be left to farmers.
Bureau changes to cluster development. We will implement the promotion of agricultural product processing industry, support farmers’ cooperatives and family farms to develop primary processing of agricultural products, improve the comprehensive utilization level of agricultural product processing by-products, guide large agricultural enterprises to develop deep processing of agricultural products, and basically form a pattern of gradient transfer of agricultural product processing industry to main producing areas, characteristic and advantageous producing areas, key sales areas and key logistics nodes. by2020By the end of, more than.17Ten thousand primary processing facilities for agricultural products, the postpartum loss rate of potatoes, fruits and vegetables from15% reduced tosixBelow%, processing conversion rate from2015Annual65% to2020Annualsixty-eight%。 Operating income of agricultural products processing industry is about23.5One trillion yuan, the ratio of agricultural product processing industry to total agricultural output value reached.2.4∶one.Leisure agriculture and rural tourism have developed rapidly.The multiple functions of agriculture have been continuously expanded, and new industries and formats such as shared agriculture, experience agriculture and creative agriculture have emerged in large numbers, and industries such as science and technology, culture, education, tourism and health care have merged with agriculture across borders. The implementation of leisure agriculture and rural tourism quality projects has created388A national key leisure agriculture county, identified.1216individual“One village and one scene"Beautiful leisure country. Carry out promotion activities in China and beautiful countryside, and promote them cumulatively.nine hundred and seventyA beautiful leisure village with complete functions and outstanding features and1000A boutique tourist route.2019In, the business income of leisure agriculture and rural tourism exceeded.8500100 million yuan, the average annual growth rate.9.8%, directly driven1200Increasing the employment and income of rural labor force has become an important form to expand agricultural functions and enhance rural value.Rural innovation and entrepreneurship have become a craze.The State Council issued the Opinions on Supporting Entrepreneurial Innovation of Returned Rural Workers to Promote the Integrated Development of Rural Primary, Secondary and Tertiary Industries, and supported returning migrant workers, college graduates, retired military personnel, scientific researchers and rural capable people to start businesses in their hometowns.2020In, the number of innovative entrepreneurs who returned to their hometowns reached.1010Ten thousand people, innovative entrepreneurs in the countryside.3000More than ten thousand people. Implementation of rural innovation and entrepreneurship leaders training action, held continuously.fiveAt the National New Farmers’ New Business Innovation Conference, farming experience and e-commerce live broadcast have flourished, and live broadcast agriculture has become a new bright spot in rural economy, providing new kinetic energy for the transformation of agricultural supply chain and the promotion of value chain. by2019At the end of, the number of rural e-commerce registered at or below the county level exceeded.eight hundredTen thousand, the national rural network retail sales reached1.7One trillion yuan, the total retail sales of agricultural products e-commerce reached3975100 million yuan.Rural industrial integration has gradually become a trend.Accelerate the construction of a large-scale economic circle with advantageous industrial clusters, a medium-sized economic circle with modern agricultural industrial parks, and a small economic circle with strong agricultural industries.“Yi Cun yi pin"Micro-economic circle to promote the construction of rural industries“circle"Development pattern, the formation of national, provincial, city (state), county four linkage rural industrial system, realize“Point, line and surface"Combination, organic connection of functions, and regional radiation drive. Accumulate and create characteristic advantageous industrial clusters.50National modern agricultural industrial park151Demonstration Park of Rural Industrial Integration228A town with strong agricultural industry811One, let more employment opportunities stay in the countryside and more value-added benefits be left to farmers.
Six, the green development of agriculture has been solidly promoted, and the rural ecological environment has been significantly improved.
Firmly establish Lucid waters and lush mountains are invaluable assets’s development concept, the Central Office and the State Council issued the Opinions on Innovating System and Mechanism to Promote Agricultural Green Development, further promoted the five major actions of agricultural green development and the three-year action of rural human settlements improvement, created a national agricultural green development pioneer zone, accelerated the reduction of inputs, clean production, recycling of wastes and ecologicalization of industrial models, and made great efforts to build a beautiful agricultural production environment and a clean and tidy rural living environment.The utilization intensity of agricultural resources decreased obviously.Strengthen the protection and sustainable utilization of cultivated land, water resources and biodiversity, and reasonably reduce the intensity of development and utilization of agricultural resources. We will further promote the protection and improvement of cultivated land quality, initiate the implementation of the Northeast Black Land Conservation Tillage Action Plan, steadily promote the pilot project of cultivated land rotation fallow system, and strengthen the control and remediation of cultivated land soil pollution in heavy metal pollution areas in the south.2019The average level of cultivated land quality in China reached4.76, more2014Annual promotion0.35A grade. Accelerate the national agricultural water-saving action, popularize dry farming, high-efficiency water-saving irrigation and other technologies, further improve the efficiency of water resources utilization, and reach the national high-efficiency water-saving irrigation area.3.39100 million mu, the effective utilization coefficient of farmland irrigation water reached.0.559. Strictly control the utilization of groundwater resources, and the groundwater level in parts of North China and Northeast China has stopped falling and rebounded.The production environment is cleaner.Implement chemical fertilizer reduction and efficiency improvement, green prevention and control, and organic fertilizer substitution for fruit, vegetable and tea. Major actions, such as actively promoting new technologies such as formula fertilization, simultaneous sowing of seeds and fertilizers, and integration of water and fertilizer, have led to a negative growth in the use of pesticides and fertilizers nationwide for four consecutive years.2020In, the utilization rates of pesticides and fertilizers of rice, wheat and corn reached respectively.40.6%、40.2%, respectively.2015Annual increasefourPercentage points,fivePercentage points. The State Council issued the "Opinions on Accelerating the Resource Utilization of Livestock and Poultry Breeding Wastes" to support585A large animal husbandry county promotes the resource utilization of livestock manure, and improves the utilization level from three aspects: source reduction, process control and end utilization.2019The comprehensive utilization rate of livestock manure in China reached75%, one year ahead of schedule to achieve the planning objectives, large-scale farms manure treatment facilities and equipment matching rate reached.96%。 We will further promote the pilot project of comprehensive utilization of straw focusing on the northeast region, and the comprehensive utilization rate of straw in the country will reach86.7%。 Focusing on the northwest region, we have built100A demonstration county of agricultural film recycling has vigorously promoted the application of standard plastic film, mechanized picking, specialized recycling and resource utilization, and the agricultural film recycling rate has reached.80%, key areas“white pollution"Get effective prevention and control. The quality and safety supervision level of agricultural products has been significantly enhanced, the quality and safety traceability system has been accelerated, and the qualified rate of agricultural product quality and safety monitoring has stabilized at97More than%,2020Reach the year97.8%。 Vigorously promote the certification management of green and high-quality agricultural products, and the total number of green, organic and geographical indication agricultural products in China exceeds4.35Ten thousand, the proportion of green high-quality agricultural products continued to increase.The construction of ecological system has been steadily advanced.Coordinate the management of lake and grass systems in landscape forest fields, promote the conservation and restoration of agricultural ecosystems, and achieve more stability of agricultural ecosystems and further improvement of agricultural ecological service capabilities. Solidly promote returning farmland to forests and grasslands, accelerate the implementation of natural forest resources protection, Beijing-Tianjin sandstorm source control, key shelter forest system construction and other projects, and fully implement the subsidy and reward policies for returning grazing to grasslands and grassland ecological protection.2020In 2000, the comprehensive vegetation coverage of grassland in China reached56.1%, the forest coverage rate exceeds23%, the trend of grassland desertification, desertification and rocky desertification has been initially curbed. Strengthen wetland management, carry out restoration and restoration of degraded wetlands, and maintain the national wetland area ateight100 million mu. Promote the conservation and restoration of aquatic ecology, resolutely win the tough battle of no fishing and no fishing in the Yangtze River, achieve full coverage of the closed fishing period system in seven key inland basins, and the Yangtze River basin332Three aquatic biological protection zones took the lead in realizing a comprehensive ban on fishing, and the work pattern of protecting the Yangtze River and promoting the green development of the Yangtze River Economic Belt was basically formed. The total management system of marine fishery resources was basically established and completed ahead of schedule.“Thirteenth five-year plan"The number of marine fishing boats has been reduced, fishery resources have been rehabilitated, the protection of aquatic wild animals and their habitats has been significantly improved, and the beach environment in offshore aquaculture waters has been significantly improved.The living environment in rural areas has improved significantly.Study Zhejiang deeply.“Demonstration of thousands of villages and renovation of thousands of villages"Engineering experience, adjust measures to local conditions, continue to exert strength, fully promote the key tasks of rural human settlements improvement, organize the implementation of village cleaning actions, and focus on rectifying the dirty and messy rural environment. Solidly promote the rural toilet revolution, establish and improve the rural toilet construction and management mechanism, integrate and promote a number of rural toilet improvement models suitable for different regions, and focus on the harmless treatment and resource utilization of rural toilet manure. Promote rural sewage treatment and manure treatment as a whole, implement unified planning, unified construction, unified operation and unified management of rural domestic sewage treatment at county level, strengthen the treatment of black and odorous water bodies in rural areas, and accumulate rural sewage treatment facilities.50More than ten thousand sets. Comprehensively promote the construction of rural domestic waste collection, transportation and disposal system, actively promote the classification of rural domestic waste, and accumulate domestic waste collection, transshipment and treatment facilities.450More than ten thousand (vehicles). by2020By the end of, the penetration rate of rural sanitary toilets in China exceeded.sixty-eight%, rural domestic waste collection, transportation and disposal system coverage90The level of domestic sewage treatment in more than% administrative villages and rural areas has been continuously improved.95More than% of the villages have carried out clean-up operations, basically achieving clean and tidy villages.
Major actions, such as actively promoting new technologies such as formula fertilization, simultaneous sowing of seeds and fertilizers, and integration of water and fertilizer, have led to a negative growth in the use of pesticides and fertilizers nationwide for four consecutive years.2020In, the utilization rates of pesticides and fertilizers of rice, wheat and corn reached respectively.40.6%、40.2%, respectively.2015Annual increasefourPercentage points,fivePercentage points. The State Council issued the "Opinions on Accelerating the Resource Utilization of Livestock and Poultry Breeding Wastes" to support585A large animal husbandry county promotes the resource utilization of livestock manure, and improves the utilization level from three aspects: source reduction, process control and end utilization.2019The comprehensive utilization rate of livestock manure in China reached75%, one year ahead of schedule to achieve the planning objectives, large-scale farms manure treatment facilities and equipment matching rate reached.96%。 We will further promote the pilot project of comprehensive utilization of straw focusing on the northeast region, and the comprehensive utilization rate of straw in the country will reach86.7%。 Focusing on the northwest region, we have built100A demonstration county of agricultural film recycling has vigorously promoted the application of standard plastic film, mechanized picking, specialized recycling and resource utilization, and the agricultural film recycling rate has reached.80%, key areas“white pollution"Get effective prevention and control. The quality and safety supervision level of agricultural products has been significantly enhanced, the quality and safety traceability system has been accelerated, and the qualified rate of agricultural product quality and safety monitoring has stabilized at97More than%,2020Reach the year97.8%。 Vigorously promote the certification management of green and high-quality agricultural products, and the total number of green, organic and geographical indication agricultural products in China exceeds4.35Ten thousand, the proportion of green high-quality agricultural products continued to increase.The construction of ecological system has been steadily advanced.Coordinate the management of lake and grass systems in landscape forest fields, promote the conservation and restoration of agricultural ecosystems, and achieve more stability of agricultural ecosystems and further improvement of agricultural ecological service capabilities. Solidly promote returning farmland to forests and grasslands, accelerate the implementation of natural forest resources protection, Beijing-Tianjin sandstorm source control, key shelter forest system construction and other projects, and fully implement the subsidy and reward policies for returning grazing to grasslands and grassland ecological protection.2020In 2000, the comprehensive vegetation coverage of grassland in China reached56.1%, the forest coverage rate exceeds23%, the trend of grassland desertification, desertification and rocky desertification has been initially curbed. Strengthen wetland management, carry out restoration and restoration of degraded wetlands, and maintain the national wetland area ateight100 million mu. Promote the conservation and restoration of aquatic ecology, resolutely win the tough battle of no fishing and no fishing in the Yangtze River, achieve full coverage of the closed fishing period system in seven key inland basins, and the Yangtze River basin332Three aquatic biological protection zones took the lead in realizing a comprehensive ban on fishing, and the work pattern of protecting the Yangtze River and promoting the green development of the Yangtze River Economic Belt was basically formed. The total management system of marine fishery resources was basically established and completed ahead of schedule.“Thirteenth five-year plan"The number of marine fishing boats has been reduced, fishery resources have been rehabilitated, the protection of aquatic wild animals and their habitats has been significantly improved, and the beach environment in offshore aquaculture waters has been significantly improved.The living environment in rural areas has improved significantly.Study Zhejiang deeply.“Demonstration of thousands of villages and renovation of thousands of villages"Engineering experience, adjust measures to local conditions, continue to exert strength, fully promote the key tasks of rural human settlements improvement, organize the implementation of village cleaning actions, and focus on rectifying the dirty and messy rural environment. Solidly promote the rural toilet revolution, establish and improve the rural toilet construction and management mechanism, integrate and promote a number of rural toilet improvement models suitable for different regions, and focus on the harmless treatment and resource utilization of rural toilet manure. Promote rural sewage treatment and manure treatment as a whole, implement unified planning, unified construction, unified operation and unified management of rural domestic sewage treatment at county level, strengthen the treatment of black and odorous water bodies in rural areas, and accumulate rural sewage treatment facilities.50More than ten thousand sets. Comprehensively promote the construction of rural domestic waste collection, transportation and disposal system, actively promote the classification of rural domestic waste, and accumulate domestic waste collection, transshipment and treatment facilities.450More than ten thousand (vehicles). by2020By the end of, the penetration rate of rural sanitary toilets in China exceeded.sixty-eight%, rural domestic waste collection, transportation and disposal system coverage90The level of domestic sewage treatment in more than% administrative villages and rural areas has been continuously improved.95More than% of the villages have carried out clean-up operations, basically achieving clean and tidy villages.
Seven, the rural reform has been comprehensively deepened, and the vitality of factors and development momentum have been further stimulated.
Always regard reform and innovation as the fundamental driving force of rural development, proceed from the deep-seated contradictions in agricultural and rural development, and unremittingly promote rural reform and institutional innovation around key areas and key links to effectively liberate and develop rural productive forces.The reform of rural land system has been steadily advanced.In line with the wishes of farmers to retain the right to contract land and transfer the right to operate land, the Central Office and the State Council issued the "Implementation Opinions on Improving the Measures for Separating the Right to Contract and Operate Rural Land", which established that rural contracted land should adhere to collective ownership, stabilize farmers’ contracting rights and liberalize land management rights.“Sanquan"The split system arrangement is another great innovation after the household contract responsibility system. The Central Committee of the Communist Party of China and the State Council issued the "Opinions on Maintaining the Stability and Long-term Invariance of Land in contract relationship", clarifying the connotation of long-term invariance and the basic principles of extending the second round of land contract after its expiration, and organizing it according to the requirements of the central authorities.16A provincetwentyCounty-level61A village (group) carried out the pilot project of extending the package first. Actively carry out the registration and certification of land contractual management rights, the whole country2838A county,3.4Ten thousand villages and towns,55More than 10,000 administrative villages have basically completed this work.15One hundred million mu of contracted land is confirmed to the contracted farmers, which is close.2Hundreds of millions of farmers have issued certificates of land contractual management rights, and the certification rate has exceeded96%, to ensure the stability of land in contract relationship, really let farmers eat.“Long-acting reassurance". Start a new round of pilot reform of rural homestead system, and explore the ownership, qualification and use right of homestead.“Sanquan"Split implementation form.The reform of rural collective property rights system has been comprehensively promoted.The Central Committee of the Communist Party of China and the State Council issued the Opinions on Steadily Promoting the Reform of Rural Collective Property Rights System, which further clarified rural collective property rights, guided farmers to develop joint-stock cooperation, and endowed farmers with relevant rights and interests in rural collective assets. The verification of rural collective assets was basically completed, and the collective land resources were checked and verified.65.5100 million mu, book assets6.5One trillion yuan, realized.“Clear accounts at the end". The reform of the joint-stock cooperative system of operating assets was promoted in an orderly manner, and collective members were confirmed.sixMore than 100 million people,43.8Ten thousand villages have completed reforms, among which41.3Ten thousand villages received the registration certificate of collective economic organizations,2019In 2000, the collective income of villages in China exceededfiveVillages with more than 10 thousand yuan account for48.2%, the collective members accumulated dividends more than3800100 million yuan. Agricultural support and protection policies have been continuously improved. Adhere to the problem orientation, promote the gradual shift from relying solely on finance to three-dimensional policy supply, and gradually establish an agricultural support and protection system covering the whole process of agricultural production, circulation, storage and consumption of agricultural products and agricultural products trade. Improve the price formation mechanism of agricultural products, and successively implement the target price subsidies for soybeans and cotton.“Separation of market pricing and price compensation", cancel the policy of temporary storage of corn, establish“Market acquisition+Producer subsidy"System. We will basically establish an agricultural subsidy policy system oriented to green ecology, promote the rational utilization of agricultural resources and protect the ecological environment, and comprehensively promote direct subsidies for grain production, subsidies for improved crops and comprehensive subsidies for agricultural materials.“Integration of three supplements"Reform, support the protection of cultivated land fertility and moderate scale operation of grain. Agricultural insurance has been expanded, quality improved, agricultural catastrophe insurance pilot, three major food crops full cost insurance and income insurance pilot, and the central government’s pilot program for rewarding local agricultural products with local advantages and characteristics.“Thirteenth five-year plan"During the period, it has provided risk protection for the agricultural industry.12.2One trillion yuan, serving farmers8.02Hundreds of millions of households. Basic construction of multi-level agricultural risk guarantee mechanism. The national agricultural credit guarantee system is basically sound,2020National agricultural credit guarantee system in insurance projects insixty-nineTen thousand, the insured amount2060One hundred million yuan, the policy can be enlarged.3.21Times.Other reforms in rural areas have been steadily advanced.whole country34The tasks of public security inspection law and basic education reform in this reclamation area have been fully completed, and the basic medical public health and community reform have been completed respectively.93.4% and97.4%, the actual land ownership certification area4.13100 million mu, certification rate96.2%。16The management system and modern enterprise system of the parent and subsidiary companies of the provincial agricultural reclamation groups with capital as the link have been further improved.18A state-owned farm belongs to the establishment of reclamation areas managed by cities and counties300More than 100 regional groups and specialized industrial companies. The operating income of Guangming Food, Shounong Food and Beidahuang Group has exceeded 100 billion yuan, and together with Tianjin, Guangdong and other agricultural reclamation groups, it has become the backbone of urban main and non-staple food supply. The reform of collective forest right system and the comprehensive reform of supply and marketing cooperatives have been promoted in coordination. System revision25Ministry of agriculture and rural areas laws and regulations and25Ministry regulations,95% of the city,90% of counties have completed the reform of comprehensive agricultural law enforcement.
The Central Committee of the Communist Party of China and the State Council issued the "Opinions on Maintaining the Stability and Long-term Invariance of Land in contract relationship", clarifying the connotation of long-term invariance and the basic principles of extending the second round of land contract after its expiration, and organizing it according to the requirements of the central authorities.16A provincetwentyCounty-level61A village (group) carried out the pilot project of extending the package first. Actively carry out the registration and certification of land contractual management rights, the whole country2838A county,3.4Ten thousand villages and towns,55More than 10,000 administrative villages have basically completed this work.15One hundred million mu of contracted land is confirmed to the contracted farmers, which is close.2Hundreds of millions of farmers have issued certificates of land contractual management rights, and the certification rate has exceeded96%, to ensure the stability of land in contract relationship, really let farmers eat.“Long-acting reassurance". Start a new round of pilot reform of rural homestead system, and explore the ownership, qualification and use right of homestead.“Sanquan"Split implementation form.The reform of rural collective property rights system has been comprehensively promoted.The Central Committee of the Communist Party of China and the State Council issued the Opinions on Steadily Promoting the Reform of Rural Collective Property Rights System, which further clarified rural collective property rights, guided farmers to develop joint-stock cooperation, and endowed farmers with relevant rights and interests in rural collective assets. The verification of rural collective assets was basically completed, and the collective land resources were checked and verified.65.5100 million mu, book assets6.5One trillion yuan, realized.“Clear accounts at the end". The reform of the joint-stock cooperative system of operating assets was promoted in an orderly manner, and collective members were confirmed.sixMore than 100 million people,43.8Ten thousand villages have completed reforms, among which41.3Ten thousand villages received the registration certificate of collective economic organizations,2019In 2000, the collective income of villages in China exceededfiveVillages with more than 10 thousand yuan account for48.2%, the collective members accumulated dividends more than3800100 million yuan. Agricultural support and protection policies have been continuously improved. Adhere to the problem orientation, promote the gradual shift from relying solely on finance to three-dimensional policy supply, and gradually establish an agricultural support and protection system covering the whole process of agricultural production, circulation, storage and consumption of agricultural products and agricultural products trade. Improve the price formation mechanism of agricultural products, and successively implement the target price subsidies for soybeans and cotton.“Separation of market pricing and price compensation", cancel the policy of temporary storage of corn, establish“Market acquisition+Producer subsidy"System. We will basically establish an agricultural subsidy policy system oriented to green ecology, promote the rational utilization of agricultural resources and protect the ecological environment, and comprehensively promote direct subsidies for grain production, subsidies for improved crops and comprehensive subsidies for agricultural materials.“Integration of three supplements"Reform, support the protection of cultivated land fertility and moderate scale operation of grain. Agricultural insurance has been expanded, quality improved, agricultural catastrophe insurance pilot, three major food crops full cost insurance and income insurance pilot, and the central government’s pilot program for rewarding local agricultural products with local advantages and characteristics.“Thirteenth five-year plan"During the period, it has provided risk protection for the agricultural industry.12.2One trillion yuan, serving farmers8.02Hundreds of millions of households. Basic construction of multi-level agricultural risk guarantee mechanism. The national agricultural credit guarantee system is basically sound,2020National agricultural credit guarantee system in insurance projects insixty-nineTen thousand, the insured amount2060One hundred million yuan, the policy can be enlarged.3.21Times.Other reforms in rural areas have been steadily advanced.whole country34The tasks of public security inspection law and basic education reform in this reclamation area have been fully completed, and the basic medical public health and community reform have been completed respectively.93.4% and97.4%, the actual land ownership certification area4.13100 million mu, certification rate96.2%。16The management system and modern enterprise system of the parent and subsidiary companies of the provincial agricultural reclamation groups with capital as the link have been further improved.18A state-owned farm belongs to the establishment of reclamation areas managed by cities and counties300More than 100 regional groups and specialized industrial companies. The operating income of Guangming Food, Shounong Food and Beidahuang Group has exceeded 100 billion yuan, and together with Tianjin, Guangdong and other agricultural reclamation groups, it has become the backbone of urban main and non-staple food supply. The reform of collective forest right system and the comprehensive reform of supply and marketing cooperatives have been promoted in coordination. System revision25Ministry of agriculture and rural areas laws and regulations and25Ministry regulations,95% of the city,90% of counties have completed the reform of comprehensive agricultural law enforcement.
Eight, the level of coordinated development between urban and rural areas continued to improve, and farmers entered a well-off society in an all-round way.
We always put the promotion of urban-rural integration and regional coordination in a prominent position, and strive to build a new system of agricultural and rural development with equal opportunities, equal services and universal results, so that farmers can equally participate in the modernization process and share the fruits of reform and development, and strive to ensure that no one falls behind on the road to a well-off society in an all-round way.The integration of urban and rural areas has progressed steadily.The Central Office and the State Council issued the Opinions on Establishing and Perfecting the System, Mechanism and Policy System of Urban-Rural Integration Development, jointly promoted new urbanization and rural revitalization, actively explored the system and mechanism of urban-rural integration development in line with China’s national conditions, and accelerated the construction of a new type of urban-rural relationship with comprehensive integration and common prosperity. Deepen the reform of the household registration system, the threshold for agricultural transfer population to settle in cities is constantly decreasing, and the channels are gradually widened, exceedingone100 million agricultural transfer population settled in cities and towns, and the urbanization rate broke through.60%。 Adhere to the integrated planning of urban and rural infrastructure, and comprehensively improve the level of infrastructure such as rural hydropower network.99.61% of administrative villages are connected with hardened roads, and farmers’ safe drinking water is basically guaranteed. Administrative villages are connected with optical fibers and roads.4GThe proportion exceeds98%。 The supply mechanism of basic public services in urban and rural areas has been accelerated, the guarantee mechanism of compulsory education in urban and rural areas has been initially established, and medical institutions and personnel in rural areas have been established“blank spot"Basically eliminated, a unified system of basic old-age insurance, basic medical insurance and serious illness insurance for urban and rural residents was gradually established.The coordination of regional agricultural development has been further enhanced.Orderly implement the national overall strategy for regional development and vigorously promote the high-quality development of regional agriculture. We will implement the strategic requirements of taking the lead in the east, developing the west, revitalizing the northeast and rising the central region, and promote the development of comparative advantages among regions and the formation of a pattern of division of labor and cooperation. The eastern region plays a leading role in demonstration, and the level of agricultural modernization is at the forefront of the country; The northeast and central regions give full play to the advantages of better matching of water and soil resources, and the comprehensive agricultural production capacity is steadily improved.“Daliangcang"The position is further consolidated; The western region has intensified ecological construction, accelerated the transformation and upgrading of agriculture and animal husbandry, and continuously improved the level of agricultural sustainable development. Actively support the coordinated development of Beijing-Tianjin-Hebei, the integration of the Yangtze River Delta, and the construction of Guangdong-Hong Kong-Macao Greater Bay Area and the Yangtze River Economic Belt, promote industrial coordination, market coordination, scientific and technological coordination, ecological coordination and urban-rural coordination in various regions, and gradually form a development pattern with the same goal, integrated measures, complementary advantages and linked interests, and the positioning objectives of modern agriculture development in key regions are becoming increasingly clear.Significant progress has been made in the development of characteristic industries in poverty-stricken areas.Never fold Without deducting the task of tackling poverty and taking the development of industry as the fundamental policy to achieve poverty alleviation, the Ministry of Agriculture and Rural Affairs and nine departments jointly issued the "Guiding Opinions on Developing Characteristic Industries in Poverty-stricken Areas to Promote Accurate Poverty Alleviation" to promote832Five poverty-stricken counties have completed the planning of poverty alleviation industries, and the cumulative implementation of poverty alleviation industrial projects has exceeded100More than 10,000 poverty alleviation industrial bases have been built10Ten thousand, every poverty-stricken county has formed.2~threeA leading poverty alleviation industry with distinctive characteristics and a wide range of poverty, the hematopoietic function in poverty-stricken areas has been significantly improved. A large number of leading enterprises with poverty have grown in poor areas.“corporate champion+cooperation+needy/poor family"The interest linkage mechanism and the production and marketing mechanism of agricultural products have been continuously improved, and the circulation and sales channels of poverty alleviation products have been further broadened. The effect of industrial poverty alleviation is fully manifested.90More than% of the poverty-stricken households who set up files and set up cards have been supported by industrial poverty alleviation and employment poverty alleviation.2/3The above-mentioned poor households mainly rely on migrant workers and industries to get rid of poverty, and industrial poverty alleviation has become the most extensive, population-driven and sustainable poverty alleviation measure. According to experts’ calculation, the contribution rate of industrial development to the income increase of poor households has reached57%。The income level of farmers has increased rapidly.Always do everything possible
Without deducting the task of tackling poverty and taking the development of industry as the fundamental policy to achieve poverty alleviation, the Ministry of Agriculture and Rural Affairs and nine departments jointly issued the "Guiding Opinions on Developing Characteristic Industries in Poverty-stricken Areas to Promote Accurate Poverty Alleviation" to promote832Five poverty-stricken counties have completed the planning of poverty alleviation industries, and the cumulative implementation of poverty alleviation industrial projects has exceeded100More than 10,000 poverty alleviation industrial bases have been built10Ten thousand, every poverty-stricken county has formed.2~threeA leading poverty alleviation industry with distinctive characteristics and a wide range of poverty, the hematopoietic function in poverty-stricken areas has been significantly improved. A large number of leading enterprises with poverty have grown in poor areas.“corporate champion+cooperation+needy/poor family"The interest linkage mechanism and the production and marketing mechanism of agricultural products have been continuously improved, and the circulation and sales channels of poverty alleviation products have been further broadened. The effect of industrial poverty alleviation is fully manifested.90More than% of the poverty-stricken households who set up files and set up cards have been supported by industrial poverty alleviation and employment poverty alleviation.2/3The above-mentioned poor households mainly rely on migrant workers and industries to get rid of poverty, and industrial poverty alleviation has become the most extensive, population-driven and sustainable poverty alleviation measure. According to experts’ calculation, the contribution rate of industrial development to the income increase of poor households has reached57%。The income level of farmers has increased rapidly.Always do everything possible As the central task of agricultural and rural work, promoting farmers’ continuous income increase, under the impetus of various national policies to strengthen agriculture, benefit farmers and enrich farmers, constantly stabilize the basic market, broaden the scope of income increase, improve the point of income increase, tap the potential of income increase within agriculture, obtain the value-added benefits of the integration of rural primary, secondary and tertiary industries, stimulate the development vitality of new industries and new formats, and share the dividends of rural reform. The diversified growth trend of farmers’ income is obvious.“Thirteenth five-year plan"During this period, farmers’ income continued to grow rapidly.2020The per capita disposable income of rural residents reached17131Yuan, the average annual real growthsix%, one year ahead of schedule to achieve the goal of doubling. Income ratio of urban and rural residents2015Annual2.73Decline steadily to2.56. In the same period, the per capita consumption expenditure of rural residents by9223Yuan raised to13713Yuan, the average annual real growth8.3%, farmers’ sense of well-being has improved significantly.
As the central task of agricultural and rural work, promoting farmers’ continuous income increase, under the impetus of various national policies to strengthen agriculture, benefit farmers and enrich farmers, constantly stabilize the basic market, broaden the scope of income increase, improve the point of income increase, tap the potential of income increase within agriculture, obtain the value-added benefits of the integration of rural primary, secondary and tertiary industries, stimulate the development vitality of new industries and new formats, and share the dividends of rural reform. The diversified growth trend of farmers’ income is obvious.“Thirteenth five-year plan"During this period, farmers’ income continued to grow rapidly.2020The per capita disposable income of rural residents reached17131Yuan, the average annual real growthsix%, one year ahead of schedule to achieve the goal of doubling. Income ratio of urban and rural residents2015Annual2.73Decline steadily to2.56. In the same period, the per capita consumption expenditure of rural residents by9223Yuan raised to13713Yuan, the average annual real growth8.3%, farmers’ sense of well-being has improved significantly.
Looking back on the "Thirteenth Five-Year Plan", it is a five-year period in which the concept of agricultural modernization has become more advanced, the path has become clearer, and the model has become richer. It is a five-year period in which agricultural transformation and upgrading have been rapid and the quality and efficiency have been significantly improved. It is a five-year period in which farmers have benefited a lot and their fair development opportunities and rights have been better guaranteed. Achievements are inspiring, and experience is even more precious. For five years, we haveAlways adhere to comprehensively strengthen the party’s leadership, and constantly promote the theoretical innovation, practical innovation and institutional innovation of "agriculture, rural areas and farmers".The key to the success of rural affairs lies in the Party. During the "Thirteenth Five-Year Plan" period, the CPC Central Committee with the Supreme Leader as the core has always emphasized that solving the "three rural issues" is the top priority of the whole party’s work, formulated the "Regulations on Rural Work in the Communist Party of China (CPC)", improved the party’s leadership system and institutional system for rural work, established a "five-level" secretary’s work mechanism for rural revitalization, and innovatively put forward a series of major ideological and major tasks, such as promoting the structural reform of the agricultural supply side, implementing the rural revitalization strategy, adhering to the priority development of agriculture and rural areas, and promoting the integrated development of urban and rural Practice has proved that the great achievements made in agriculture and rural areas in the 13th Five-Year Plan lie in always upholding and improving the Party’s leadership over rural work, implementing the correct line, principles and policies concerning agriculture, rural areas and farmers, and guiding the development of agriculture and rural areas.Always adhere to the implementation of the new development concept and promote the coordinated development of the three major systems of modern agriculture.Idea is the forerunner of action. During the "Thirteenth Five-Year Plan" period, agricultural modernization adhered to the five development concepts of "innovation, coordination, green, openness and sharing", taking "innovation" as the first driving force for agricultural production development, optimization of management mode and construction of industrial system, "coordination" as the endogenous way to optimize structure, improve quality and fill shortcomings, and "green" as the universal form to realize agricultural resource conservation and environment-friendly development. Practice has proved that the new development concept is a strategic idea of managing the overall situation, managing the root and managing the long term. It is under the guidance of this concept that agriculture and rural areas have always maintained the correct development direction and kept steady and far-reaching in the complicated and severe internal and external environmental changes.Always persist in deepening reform and constantly stimulate the vitality of resources, factors and markets.Reform is the magic weapon to promote development. Since the "Thirteenth Five-Year Plan", we have always regarded reform as the fundamental driving force for the development of agriculture, countryside and farmers. In accordance with the requirements of "expanding, speeding up and integrating", we have persistently promoted rural reform and institutional innovation, strived to get rid of the shortcomings of institutional mechanisms, and made great efforts to break through the barriers of solidification of interests. The factors of agricultural production resources have been continuously activated, and the endogenous driving force of rural development has been continuously stimulated, which has brought about historic changes in rural economic and social development. Practice has proved that only by persisting in emancipating the mind, deepening reform and correctly handling the relationship between farmers and land, farmers and collectives, and farmers and citizens can we inject a steady stream of powerful impetus into the development of agriculture and rural areas.Always respect the dominant position of farmers and promote the modernization of farmers in agriculture and rural areas.Firmly establishing the people-centered development thought and safeguarding farmers’ material rights and democratic rights are the fundamental starting point and foothold of the work concerning agriculture, countryside and farmers. Since the "Thirteenth Five-Year Plan", we have taken the development of rural industries as an important way to promote farmers’ employment and income, taken the improvement of rural living environment as a major project to improve farmers’ quality of life, and taken tackling poverty as a key measure for farmers to run a well-off society in an all-round way. We have always insisted on developing for farmers, relying on farmers for development, and sharing the fruits of development with farmers. Practice has proved that only by fully respecting farmers’ initiative and realizing, safeguarding and developing the fundamental interests of farmers can the enthusiasm, initiative and creativity of hundreds of millions of farmers be stimulated, and the stability of agricultural production and the harmonious and orderly rural society can be effectively guaranteed.Always adhere to the convergence of efforts and guide the formation of a multi-participation pattern of government, market and farmers.To promote agricultural modernization, we must mobilize all forces and gather all wisdom. Since the "Thirteenth Five-Year Plan", we have actively promoted the construction of national modern agricultural demonstration zones, modern industrial parks, industrial towns, etc., widely adopted the methods of government guidance, enterprise drive and farmers’ participation, further clarified the role of the government in institutional arrangements, strengthened the top-level design, played the decisive role of the market in resource allocation, allowed the free flow of capital, labor and other production factors, improved the degree of farmers’ production organization, and built a new pattern in which the government, the market and farmers jointly promoted agricultural modernization. Practice has proved that only by introducing multi-party resources, bringing together multi-party efforts, and letting all kinds of subjects develop their strengths and benefit from each other, can we unify our goals and directions and achieve the goal of win-win cooperation.
Summarizing history is to better face the future. The "Fourteenth Five-Year Plan" period is the first five years after China has built a well-off society in an all-round way and achieved the first century-long struggle goal, taking advantage of the situation to start a new journey of building a socialist modern country in an all-round way and March towards the second century-long struggle goal. Benchmark2035The goal of socialist modernization was basically achieved in, agricultural and rural development is still the biggest shortcoming of economic and social development and the most prominent short leg of national modernization, and the situation of poor foundation, weak foundation and backward development of agriculture has not fundamentally changed. Looking forward to the "14th Five-Year Plan", the world is in an accelerated evolution period, the COVID-19 epidemic has a wide impact, the strategic game of big countries has become the norm, the domestic economy is in the crucial stage of changing the development mode, optimizing the economic structure and transforming the growth momentum, and the internal and external environment for agricultural and rural development is more complex and changeable. Danger and opportunity coexist, and opportunities lie in challenges, and challenges contain opportunities. We will unite more closely around the CPC Central Committee with the Supreme Leader as the core, take Socialism with Chinese characteristics Thought of the Supreme Leader in the new era as the guide, aim at the big goal of basically realizing the modernization of agriculture and rural areas, unswervingly implement the new development concept, closely follow the requirements of promoting high-quality development and building a new development pattern, adhere to the priority development of agriculture and rural areas, fully implement the rural revitalization strategy, comprehensively accelerate the modernization of agriculture and rural areas, and further consolidate the foundation of modern agriculture. Adjust and optimize the agricultural structure, promote various forms of moderate scale operation, continuously improve the security level of important agricultural products such as grain, focus on improving the quality, efficiency and competitiveness of agriculture, and write a new cadenza for agricultural and rural reform and development in the new journey of promoting the comprehensive revitalization of rural areas and realizing the goal of the second century!